LDAP (Lightweight Directory Access Protocol)
LDAP (Lightweight Directory Access Protocol) is a directory access protocol used to query and manage information stored hierarchically, such as identity and user authentication information in corporate networks.
In this tutorial, we will demonstrate how to configure Parkpow to provide the option of user authentication through LDAP, leveraging the benefits of this protocol to efficiently and securely manage identity information.
LDAP configuration
Follow the steps below to configure Parkpow on your LDAP server
To make this configuration, always have the latest version of Parkpow on-premise. Follow the procedure here to install the latest version
Go to Settings > Users > Configure LDAP
To begin the configuration, go to Settings > Users. In the upper right corner, a "Configure LDAP" button should appear, as shown in the image below:
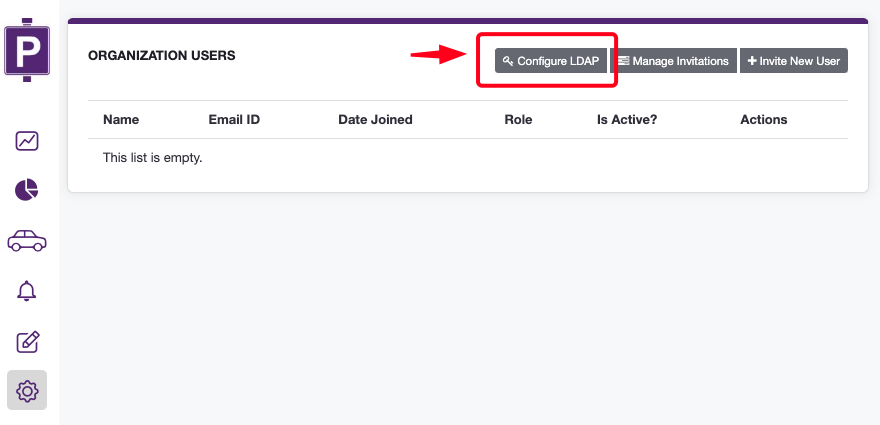
If the button is not available, please upgrade to the latest version of Parkpow on-premise.
Configure LDAP Settings
Fill in the fields with the settings related to your server.
Server URL:
This setting refers to the LDAP server address you want to access. Typically, the URL will include the protocol (LDAP or LDAPS), the domain name or IP address of the server, and the port if you're not using the default port.
Example:
ldap://192.168.0.10:389
Bind DN (Distinguished):
The Bind DN is the Distinguished Name (DN) you use to authenticate initially to the LDAP server. Usually, it's the DN of a user with read permissions in the directory. This allows you to establish an initial connection to the server before performing user queries or authentications.
Example:
uid=admin,ou=system
The selected user should have the necessary permissions for accessing the directory hierarchy.
Bind Password:
The password corresponding to the Bind DN. This password is used to authenticate the initial connection to the LDAP server.
User Attribute Mapping (User attr map):
This setting specifies how user attributes in LDAP correlate with user attributes in your system. For example, you can map the LDAP attribute "cn" to the system's username.
Example:
{
"email": "mail",
"username": "uid",
"last_name": "sn",
"first_name": "cn"
}
The example above shows a standard configuration of an OpenLDAP server, it is important to note that the mail, uid, sn, cn fields may vary according to your LDAP server.
The email and username fields are mandatory and unique.
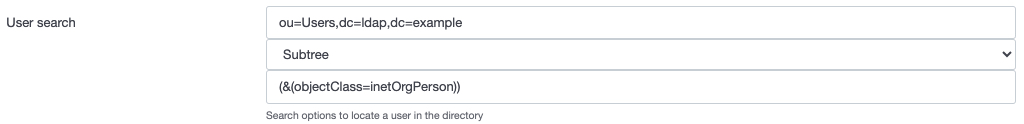
User Search:
User search configuration defines the parameters for locating and authenticating users in the LDAP directory. It includes information such as the base of search (Base DN), which is where the search begins in the directory hierarchy, and an optional search filter that restricts the results.
Example:
Connection options
This parameter should be added if your server has any specific connection settings.
Start TLS
Check this option if the server supports this feature.
Enable User Authentication
Check this option to enable/disable LDAP authentication in Parkpow.
Step 03
Save settings; Parkpow will attempt to connect to the LDAP server, and if everything goes well, the settings will be saved.
If the connection to the server is unsuccessful, the image below will be displayed.
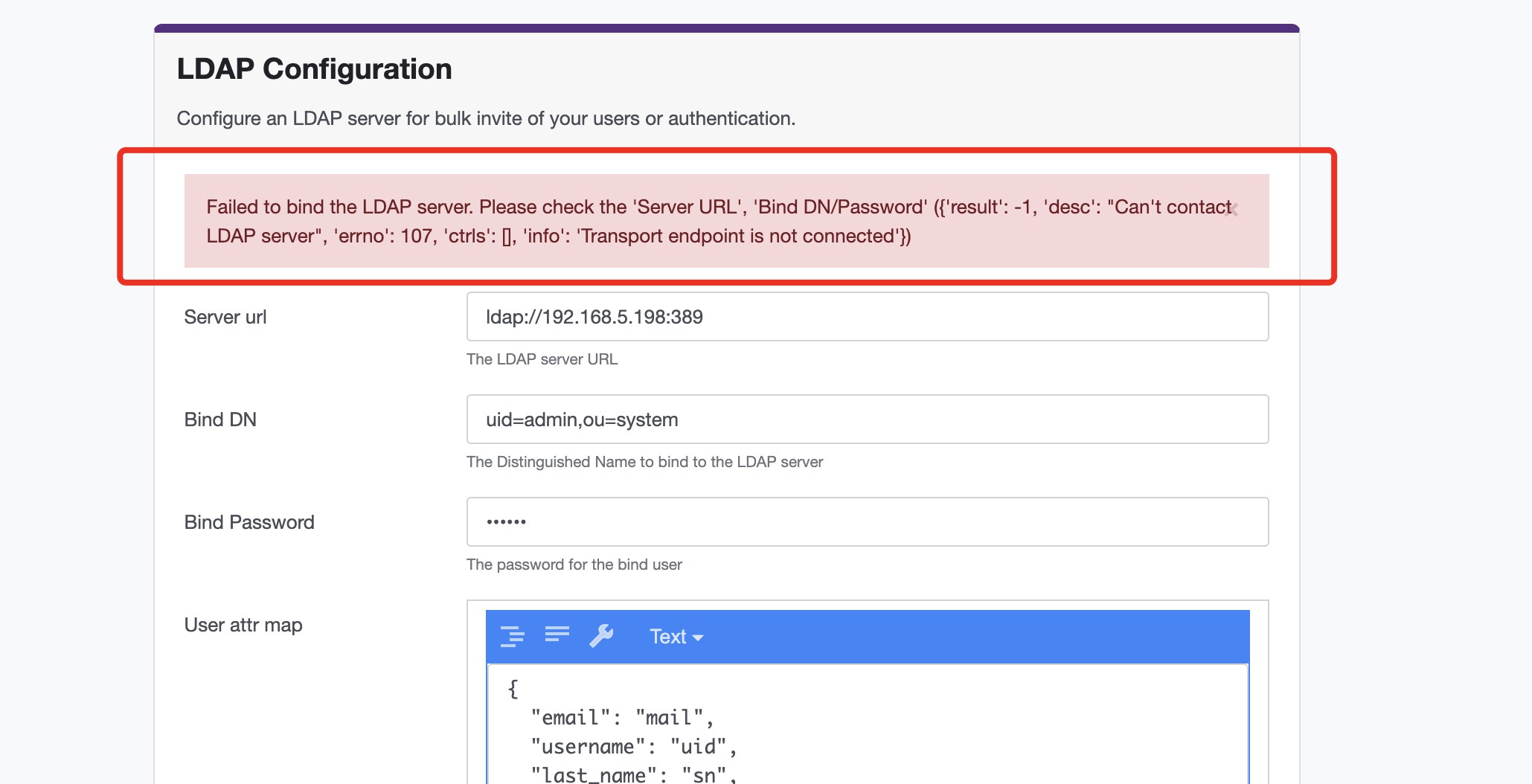
Review the settings and try saving again.
User configuration
After configuring the server, users with permissions can log in to Parkpow, and they will receive the default permission level (Viewer).
If it's necessary to change user permissions, after the user's first login, access the user settings menu and modify the permissions as needed.